Introduction
When designing Azure infrastructure, we always do our best to secure our environment and confidential data. Unfortunately, we all do mistakes. We may forget to configure something, we can face some portal issues that impact our deployment, or we can miss some knowledge that is required to configure everything securely and correctly. To avoid all that, we can use Azure Policies that assess our environment in order to find any mistakes, missing configuration or compliance issues. What is more, Azure Policies are capable of proposing steps to increase the level of security within Azure infrastructure. Unfortunately, to perform such assessment, we need to deploy and configure every resource prior, only then we receive reliable feedback from Azure policies. Such approach can lead to unnecessary costs generated by unused azure resources before we even start to use Azure components in production. On the other hand, we are capable of doing deployment of Azure stuff using Infrastucture-as-Code – For example Azure Bicep. However, creation of complex Bicep or Terraform may lead to mistakes in the configuration. Luckily, there is already a tool that can be used to perform assessment of Azure resource configuration prior to the deployment via code. That tool is named Checkov. If you are interested in what this solution is and how it works, feel free to read that short article.
Checkov
Checkov is a tool that allows you to scan and analyze our IaC files. During its execution, the tool looks for the configuration of the environment that could lead to security or compliance issues, including ISO standards. That tool already supports over 1000 built-in policies. What is more, we are able to integrate or own policies to be compared with our deployment templates. Right now, Checkov supports scanning of IaC frameworks such as: Terraform, ARM Templates, Bicep, Docker, Kubernetes, CloudFormation and Helm Charts. Mentioned tool is also skilled to do Software Composition Analysis that scans open-source images and packages used in our deployment in order to find any common vulnerabilities and exposures.
For example, Checkov is able to compare our infrastructure with well-known security standard like centre for internet security (CIS). As I already mentioned, it is also possible to create our own policies, they can be created using Python or YAML.
Additionally, we are able to integrate Checkov with Bridgecrew. That integration allows us to use checkov in our CI/CD systems or create compliance reports. The above sums up to a fascinating tool that provides a big bunch of relevant information for developers, administrators, or even managerial level.
If you would like to read more about this tool, I really encourage you to read official documentation Quick Start – checkov
Demo
Now let’s move on to the more interesting part of the article – testing the Checkov using Bicep templates. We need to start with installation of the tool. In order to do it correctly, I would recommend you to follow the official documentation. Separate instructions for different OS types available – Installing Checkov – checkov.
In my case, we will be using homebrew commands.
- Firstly, I need to open the terminal and execute the following command.
brew install checkov
2. We can test if everything went smoothly by executing the command “Checkov”. If the tool is installed correctly, then we receive similar response as below.
3. Now we will try to find some Bicep file that can be used for tests. We will use some Bicep template from Microsoft repository – azure-quickstart-templates/main.bicep at master · Azure/azure-quickstart-templates (github.com).
4. As the next step, we will start our scanning. In order to achieve that, we are executing the command shown below. Flag -d says that we are going to scan the entire folder, if we want to limit the scan to only one file we can use flag -f.
checkov -d (Directory path)
5. On the screenshot shown below, we can find a summary of the scan performed by Checkov. We can see how many steps failed and how many succeeded. In the next part, we can find more information about each step, their severity, and link to the instruction on how to solve the mentioned issues.
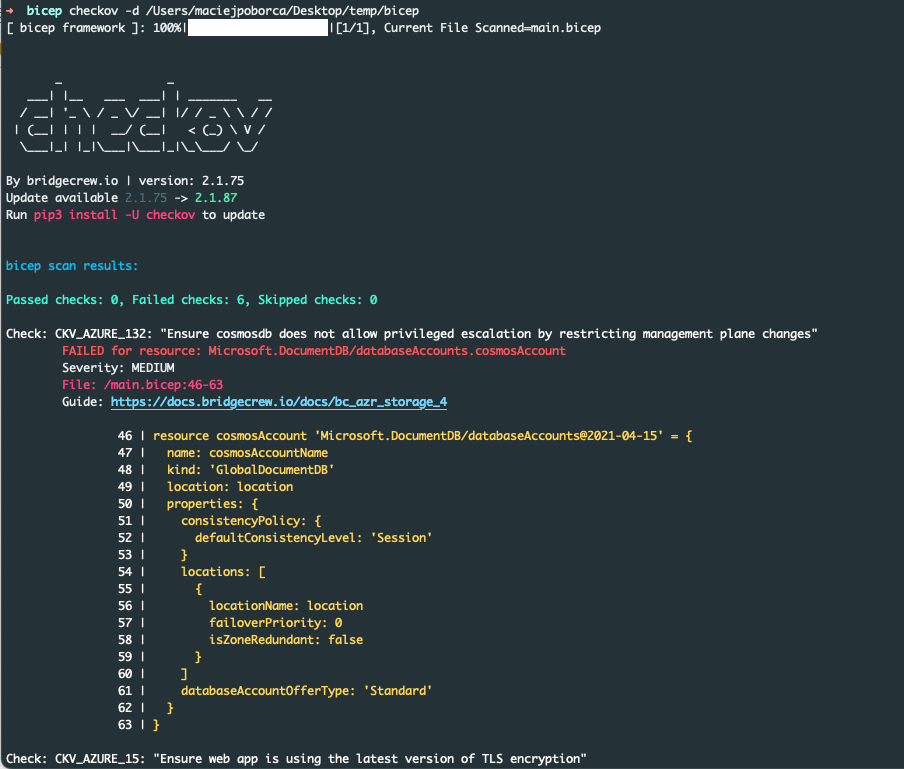
Summary
To sum up, Checkov is a very interesting tool which I’m going to use to check compliance of my .bicep files with security policies or standards. The tool is still under the development, that’s why I have faced some small issues during my tests. For example, during parsing operation of complex bicep files that contain a lot of conditionals and loops, I have received an error saying it is not possible to parse that file. Still, I think it is a fascinating tool, and you should test it if you work with IaC. If the topic was appealing to you, or you would like to see some other Azure related topics in my blog, please leave a comment.
[PL] – Azure Bicep – Skan bezpieczeństwa za pomocą Checkov • Maciej Poborca.
